Kali Linux 2023.3 Release (Internal Infrastructure & Kali Autopilot)
Table of Contents
Today we are delighted to introduce our latest release of Kali, 2023.3. This release blog post does not have the most features in it, as a lot of the changes have been behind-the-scenes, which brings a huge benefit to us and an indirect positive effect to you as end-users. It always goes without saying, but there are a number of new packages and tools as well as the standard updates. If you want to see what’s new for yourself download or upgrade if you have an existing Kali Linux installation.
The highlights of the changelog since the 2023.2 release from May:
- Internal Infrastructure - Major stack changes is under way
- Kali Autopilot - The automation attack framework has had an major overhaul
- New Tools - 9 new tools added this time round!
Internal Infrastructure
With the release of Debian 12 which came out this summer, we took this opportunity to re-work, re-design, and re-architecture our infrastructure. It is as massive as it sounds, and should not be a surprise that its not yet complete! This is where a good amount of our focus has been for this release-cycle (and also the next one unfortunately). We are hoping that the majority of it will be done by the end of the year (so we can get back to what we do best!)
This gives an excuse and the motivation to simplify our software stack as much as possible. Example, using one single:
- OS version (Debian 12)
- CDN/WAF (Cloudflare)
- Web server service (Nginx)
- Infrastructure as Code (Ansible)
We also have some other goals, and replacing certain software with others (phase #2).
At the same time, we have automated some actions such as:
- The cleaning up of suites (aka branches - kali-experimental and kali-bleeding-edge)
We are very much underway with these projects already (as bug bounty hunters may notice the changes)!
Mirror Traces
We have a new sub-domain, mirror-traces.kali.org! This is to help mirror admins for our community mirrors. This now gives everyone using it more details and insight which is useful when troubleshooting and debugging issues.
True to our word, we are doing more in the open, the git repository can be found here: gitlab.com/kalilinux/tools/mirror-status.
Packaging Tools
For a long time, we have shared our home-made scripts publicly, which is our helping aid to manage all our packages in Kali. Recently we have expanded on them by giving the existing files a refresh by adding additional features and various quality-of-life improvements, as well as including new ones.
As a recap, if you want to have a peek at some back-end development:
- Autopkgtest - Using
debciin a CI fashion, we can test packages being built.- This integrates into Britney.
- Britney2 (Git repo) - Migrates packages between all of our suites (aka branches, such as “debian-testing”, “kali-rolling”, and “kali-last-snapshot” to name a few).
- Build-Logs - Output of our images/platform as well as packages being created on each supported architecture.
- Janitor - This is our automated packager as it will apply everything from minor formatting changes to preparing an package update.
- The long term goal of this is to have it handle kali-bleeding-edge, linking into Autopkgtest.
- Package Tracker - Tracks each packages version’s history.
- Packaging CI Overview (Git repo) - Quick (and dirty) overview of our package’s CI status.
- Upstream-Watch (Git repo) - Monitors when there is an update upstream.
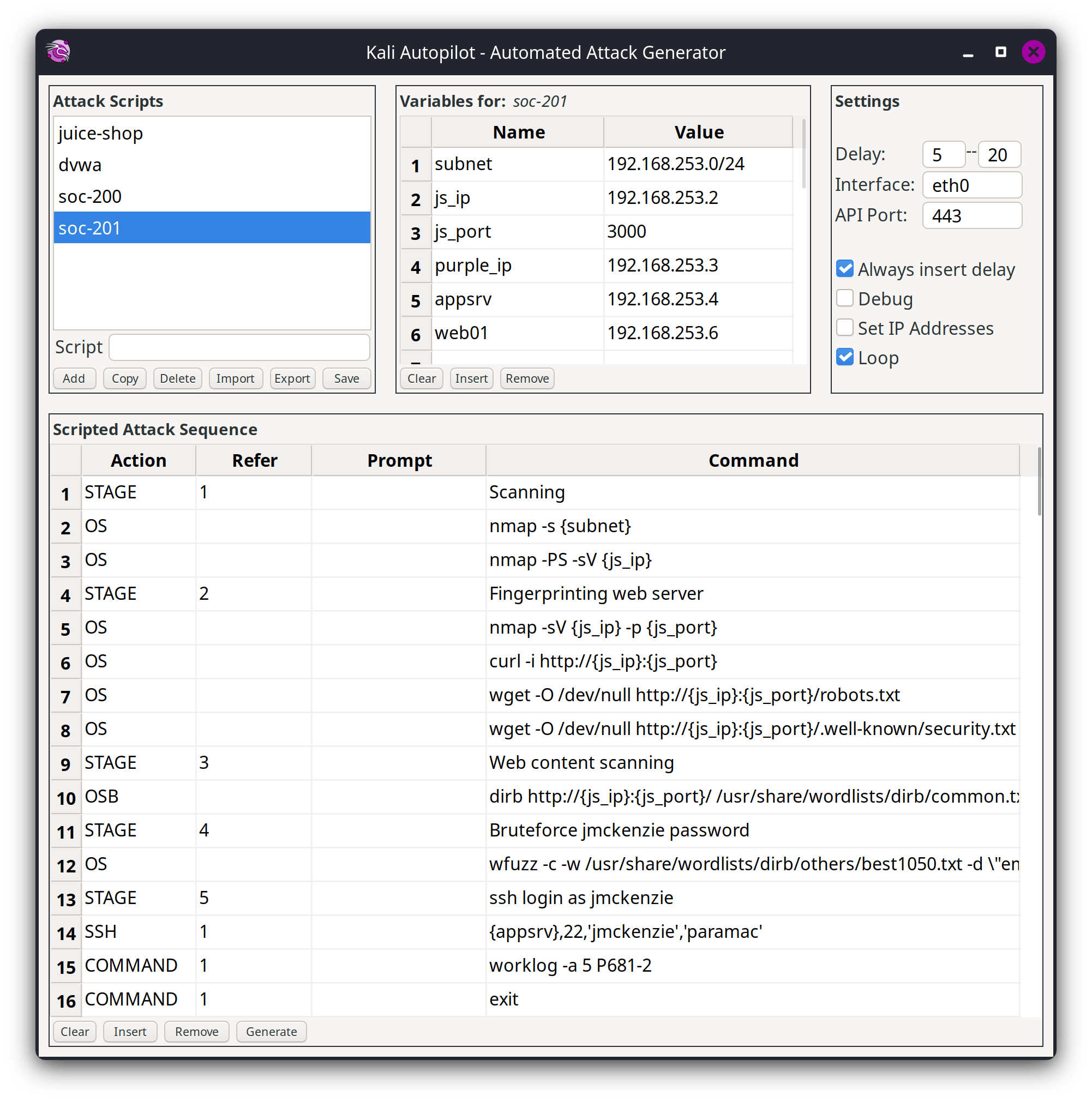
Kali Autopilot
With the release of Kali Purple in Kali 2023.1, we also had the debut of Kali Autopilot. Since then, its been worked on and is unrecognizable with its redesigned GUI and multitudinous amount of features added.
What is Kali Autopilot? We are glad you asked! Kali Autopilot is an automated attack framework. It is a bit like an “AutoPwner”, which follows pre-defined “attack scenarios”. The motivation originally started its development for the defensive side of Kali.
It is a lot easier to demonstrate Kali’s offensive side, especially when you start seeing the shells popping up. But when it comes to the defensive side, how do you know if you have set things up? You start to ask questions:
- Are the Intrusion Detection System (IDS) and the Web Application Firewall (WAF) detecting malicious activities?
- Is the Security information and event management (SIEM) ingesting the right logs?
- Are the dashboards and alerts tuned to detect attacks?
- Are the analysts trained in finding the needle in the haystack?
- Has it been tested? How can you test?
Either you can wait for someone to try and break in, or you could do it yourself. This is where Kali Autopilot comes in.
Kali Autopilot consists of a GUI tool to design attacks and to generate attack scripts that perform those attack sequences, either manually or as a service, together with a web API interface for remote control. You can also download example attack scripts from the Kali Purple Hub. We currently have scripts for juice-shop and DWVA. Just download the JSON from the hub and import it into Kali Autopilot.
This tool has come along a lot in the last 6 months, and no plans on slowing down. As always, its shaped by the community; ideas, features, and direction can be submitted and shaped by YOU. If you have developed attack scripts for vulnerable machines, we would love to include it on our Kali Purple Hub.
New Tools in Kali
We will kick it off with what’s new (to the network repositories):
- Calico - Cloud native networking and network security
- cri-tools - CLI and validation tools for Kubelet Container Runtime Interface
- Hubble - Network, Service & Security Observability for Kubernetes using eBPF
- ImHex - A Hex Editor for reverse engineers, programmers and people who value their retinas when working at 3 AM
- kustomize - Customization of kubernetes YAML configurations
- Rekono - Automation platform that combines different hacking tools to complete pentesting processes
- rz-ghidra - Deep ghidra decompiler and sleigh disassembler integration for rizin
- unblob - Extract files from any kind of container formats
- Villain - C2 framework that can handle multiple reverse shells, enhance their functionality and share them among instances
We also bumped the Kali kernel to 6.3.7.
Along with new tools being added to Kali, there has been numerous packages and libraries updates, both major and minor version such as: Greenbone, Humble, Impacket, jSQL, OWASP ZAP, Rizin, Tetragon, theHarvester, Wireshark and many many more.
Unfortunately we had to drop a few packages from Kali:
- king-phisher - The tool is no longer maintained by the original author
- As an alternative, check GoPhish as a replacement
- plecost - Tool does not work with Python 3.11, and no response from original author
- For an replacement, try WPScan
Rekono - Community Package Submission
We get a large amount of requests to add tools into Kali. We do have a policy of what tools are added to Kali and a process of how tools are packaged up and added (from network repositories to the default installed toolset). The draw back is that we do not have enough human power to be able to process them all. Our solution to this has been to help tool authors and/or anyone from the Kali community create packages by writing a series of detailed, step-by-step guides covering the complete process and workflow of how we built those packages:
- Setting up a system for packaging
- Introduction to packaging step-by-step example - Instaloader
- Intermediate packaging step-by-step example - Photon
- Advanced Packaging Step-By-Step Example - FinalRecon & Python-icmplib
- Packaging Applications with Kaboxer - “Hello World” with a Docker container
When the tool was originally submitted by the tool author, we reviewed it, liked it, and agreed it should be in Kali. We did not have the cycles to process it ourselves quick enough, but the tool author did. They step up, and then re-submitted it again with them packaging up their tool. This saved us a lot of leg work, so reviewing the package became a breeze, and shortly after was added into Kali.
If you are wanting a tool added into Kali - and you would like for it to happen sooner than we can do, have a go at trying to package yourself! There are other sources of doing “Debian packaging” out there, as well as our linked guides above. There is a initial learning curve, but its not as complex as you may think (especially if you are comfortable using Linux).
Please note, we compile packages from source. Submitting a binary *.deb file will not be accepted.
Miscellaneous
Below are a few other things which have been updated in Kali, which we are calling out which do not have as much detail:
- Added Pipewire support when using Hyper-V in enhanced session mode
- Added
kali-hidpi-modeto support Kali-Purple - Improved installation of Kali-Purple by removing the need to run any commands after installing
kali-themes-purple - Kali-Purple has a purple menu icon!
- The final reminder about the breaking change with Python 3.12 & PIP
Kali NetHunter Updates
We are proud to introduce a redesigned Kali NetHunter app and a completely new NetHunter Terminal, thanks to the amazing work of our very own @martin and @yesimxev.
On the Kali NetHunter kernel side, there are numerous updates:
- LG V20 for Lineage 19.1
- Nexus 6P for Android 8.0 (Oreo)
- Nothing Phone (1) for Android 12 (Snow cone) and 13 (Tiramisu) (new)
- Pixel 3/XL for Android 13 (Tiramisu)
- Samsung Galaxy A7 for LineageOS 18.1 (new)
- Xiaomi Mi A3 for Lineage 20
- Xiaomi Redmi 4/4X for VoltageOS 2.5
Also worth mentioning:
- By popular demand we have added a SELinux disabler.
- Please note until we are able to replace Mana Toolkit, we have had to temporary downgrade iptables.
Kali ARM Updates
The Raspberry Pi Zero W image now boots to CLI and not GUI.
This change is in line with what we did with the Raspberry Pi 1 image a few releases ago. If you do not create a wpa_supplicant.conf to use, the easiest way to connect to a Wi-Fi network on the command line is to use the nmtui command.
Alternatively, you can use sudo nmcli --ask dev wifi connect network-ssid to have it ask you for the password on the command line, without it showing up in your history.
USBArmory MKI and MKII have had their bootloaders updated to 2023.07.
The ARM build scripts have had some minor tweaks to deal with policykit updates to make sure the pkla files are properly created.
Kali Website Updates
Our Kali documentation has had various updates to existing pages as well as new pages:
- Contribute to Kali (updated)
- Deploying Kali over Network PXE Install (updated)
- Wayland (new)
A website is never complete, and our homepage is no exception. Recently we have been making some improvements:
- Get Kali - Should be a little easier to scroll and move about the page now, switching between platforms
- Partnerships - Updated to say a thank you to the new partnerships!
Since our last release, we also did the following blog posts:
Community Shout-Outs
These are people from the public who have helped Kali and the team for the last release. And we want to praise them for their work (we like to give credit where due!):
- Anutrix - who helped with kali.org/docs/
- Arszilla - who helped with i3
- Croluy - who helped with kali.org/docs/
- Pablo Santiago López - who helped with rekono-kbx
- ron190 - who helped with kali.org/tools/
- Salty_ - helping with the Raspberry Pi release testing.
Anyone can help out, anyone can get involved!
New Kali Mirrors
We have another community mirror:
- Armenia: kali.mirror1.gnc.am and kali.mirror2.gnc.am, sponsored by GNC-ALFA CJSC, thanks to Vahe Avagyan.
If you have the disk space and bandwidth, we always welcome new mirrors.
Kali Team Discord Chat
Since the launch of our Discord server with Kali 2022.3, we have been doing an hour long voice chat with a number of Kali team members. This is when anyone can ask questions (hopefully relating to Kali or the information security industry) to us.
The next session will happen a week after the release, Wednesday, 30th August 2023 16:00 -> 17:00 UTC/+0 GMT.
Please note we will not be recording this session. This is a live event only.
Get Kali Linux 2023.3
Fresh Images: Simple, Get Kali!
Did you know, we do also produce weekly builds that you can use as well. These are for people who cannot wait for our next release and you want the latest packages (or bug fixes). This way you will have fewer updates to do. Just know that these are automated builds that we do, not QA like we do for our standard release images. But we gladly take bug reports about those images because we want any issues to be fixed before our next release!
Existing Installs: If you already have an existing Kali Linux installation, remember you can always do a quick update:
┌──(kali㉿kali)-[~]
└─$ echo "deb http://http.kali.org/kali kali-rolling main contrib non-free non-free-firmware" | sudo tee /etc/apt/sources.list
[...]
┌──(kali㉿kali)-[~]
└─$ sudo apt update && sudo apt -y full-upgrade
[...]
┌──(kali㉿kali)-[~]
└─$ cp -vrbi /etc/skel/. ~/
[...]
┌──(kali㉿kali)-[~]
└─$ [ -f /var/run/reboot-required ] && sudo reboot -f
You should now be on Kali Linux 2023.3. We can do a quick check by doing:
┌──(kali㉿kali)-[~]
└─$ grep VERSION /etc/os-release
VERSION="2023.3"
VERSION_ID="2023.3"
VERSION_CODENAME="kali-rolling"
┌──(kali㉿kali)-[~]
└─$ uname -v
#1 SMP PREEMPT_DYNAMIC Debian 6.3.7-1kali1 (2023-06-29)
┌──(kali㉿kali)-[~]
└─$ uname -r
6.3.0-kali1-amd64
NOTE: The output of uname -r may be different depending on the system architecture.
As always, should you come across any bugs in Kali, please submit a report on our bug tracker. We will never be able to fix what we do not know is broken! And Social networks are not bug trackers!
Want to keep in up-to-date easier? Automate it! We have a RSS feeds and newsletter of our blog to help you.