NetHunter MANA Evil Access Point
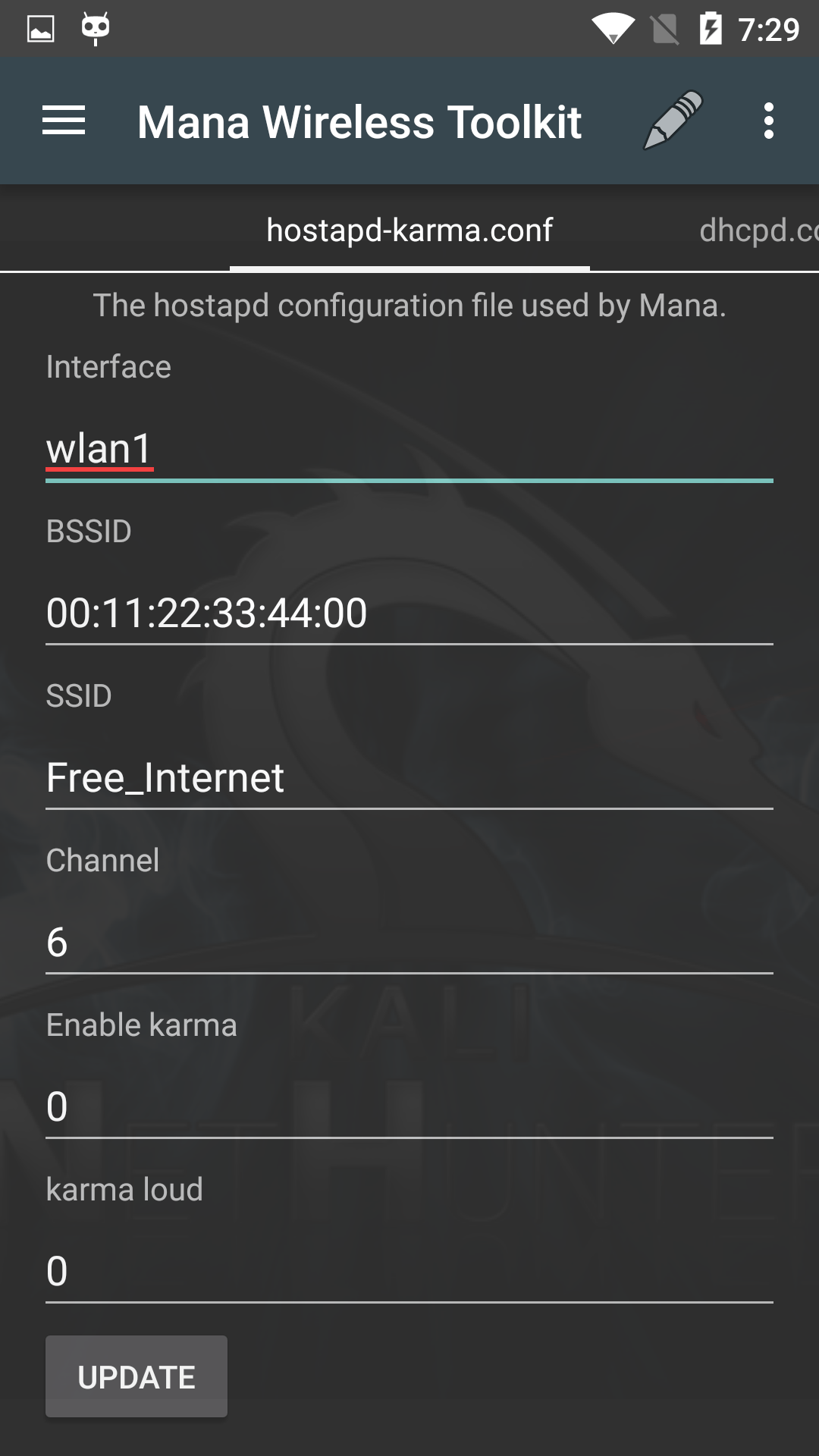
The MANA Toolkit is an evil access-point implementation by SensePost that performs rogue Wi-Fi AP and MitM attacks. The MitM logs get written to /var/lib/mana-toolkit/ in the Kali chroot.
The default MANA configuration should work as-is however, you can tweak any of the available settings to match your target environment such as the ssid, channel number, etc.
Once everything is configured to your satisfaction, tap the Update button to save the configuration.
Updated on: 2023-Jul-04
Author:
re4son